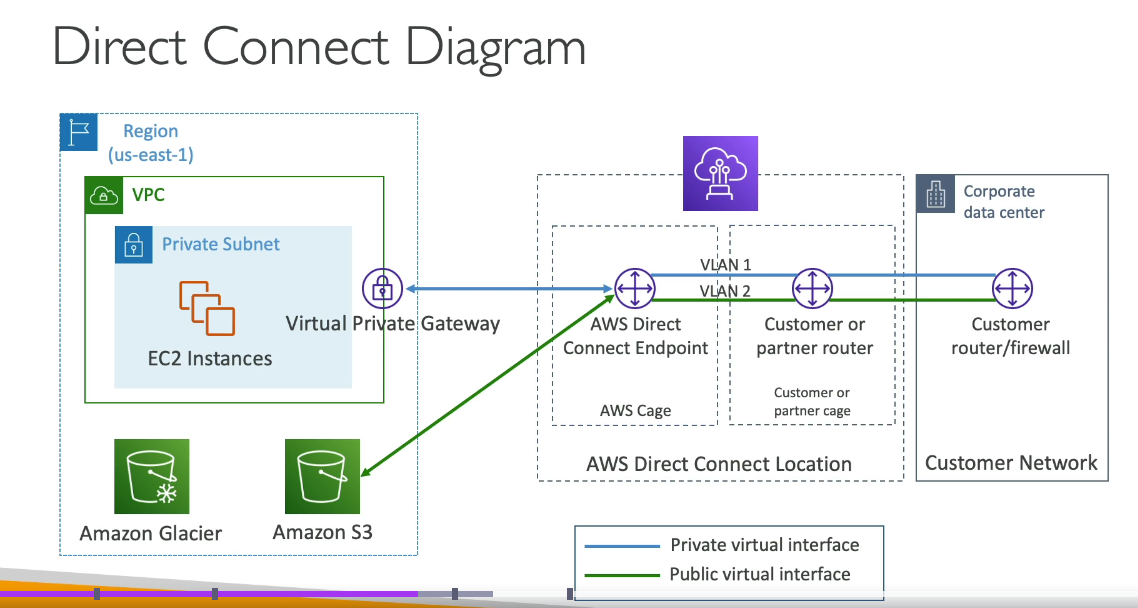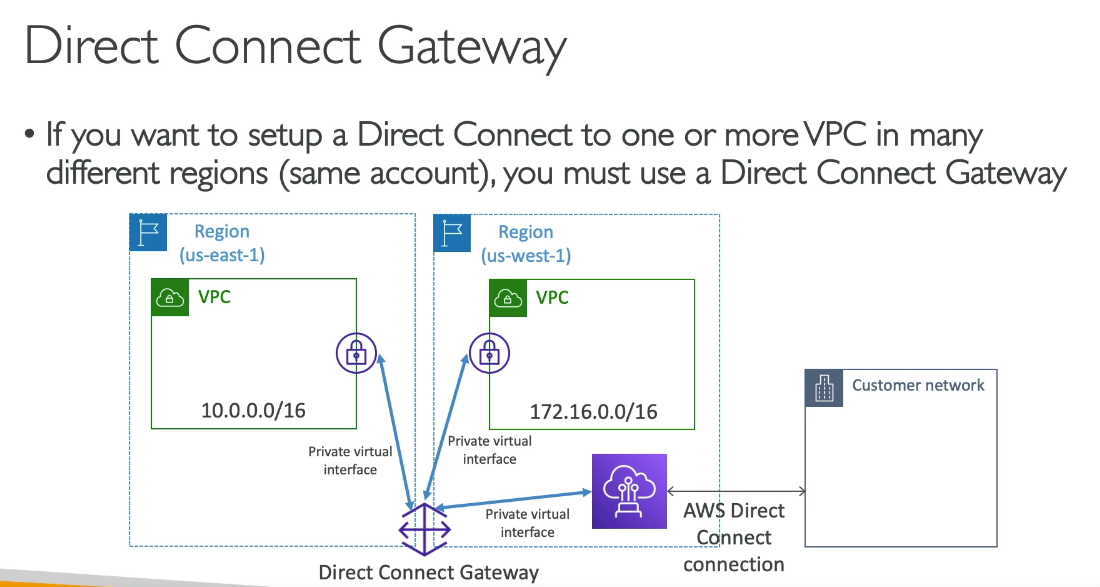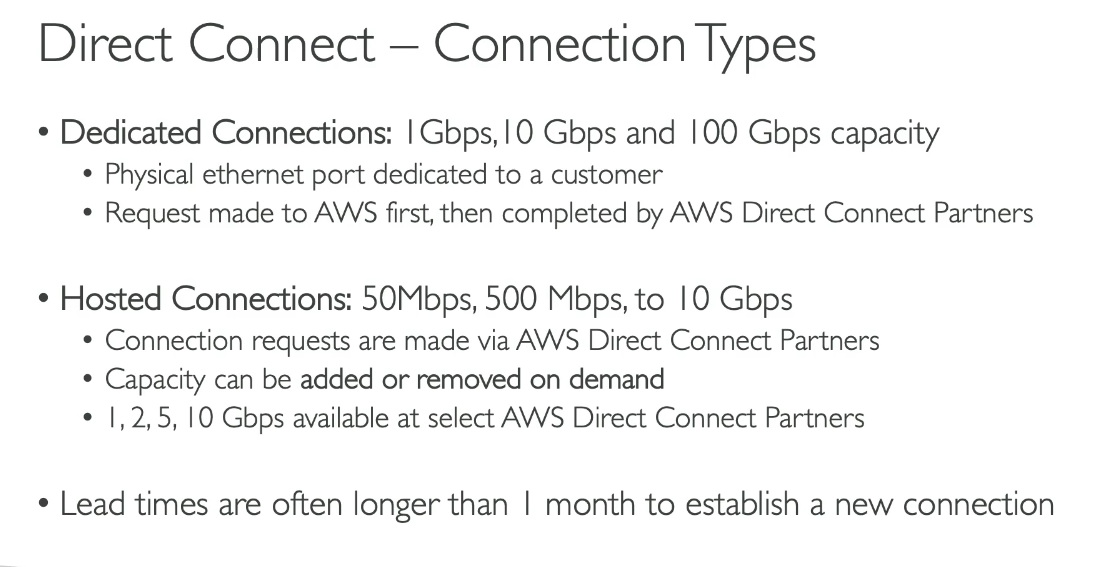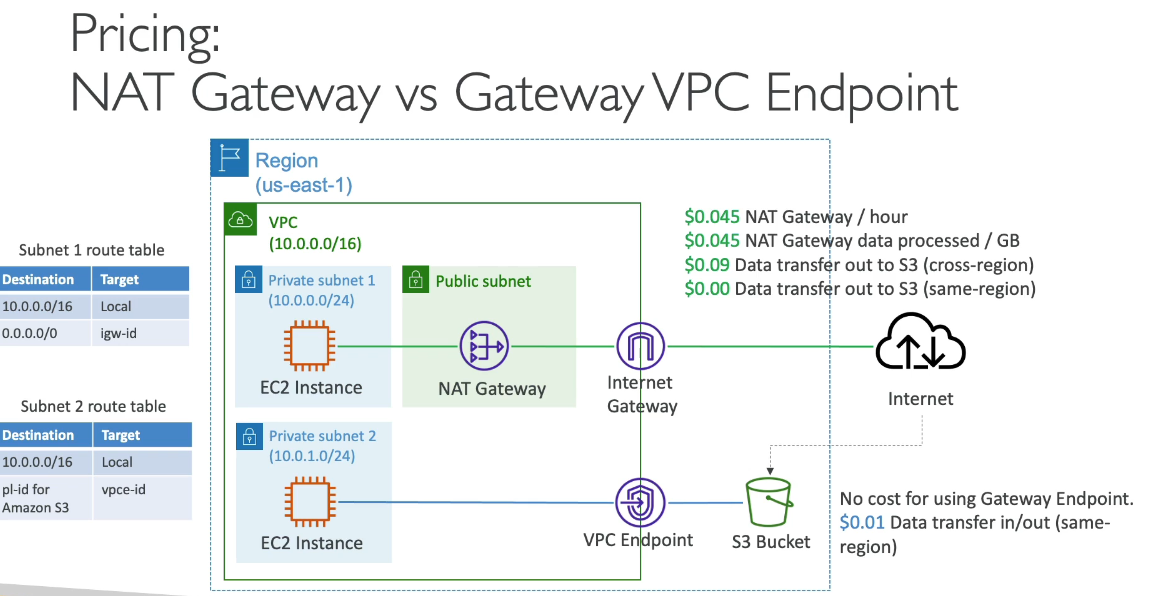
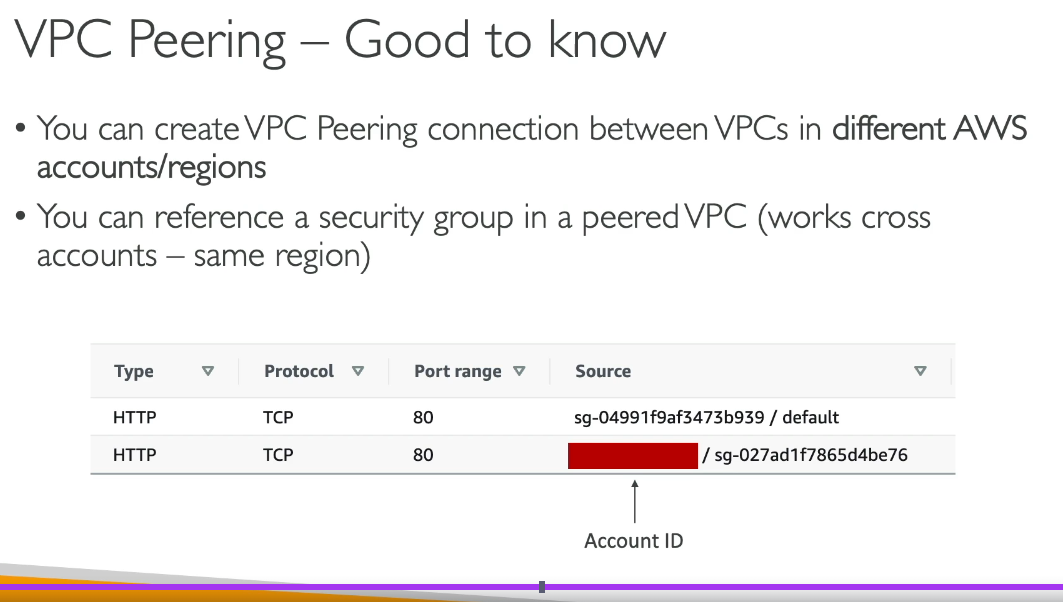
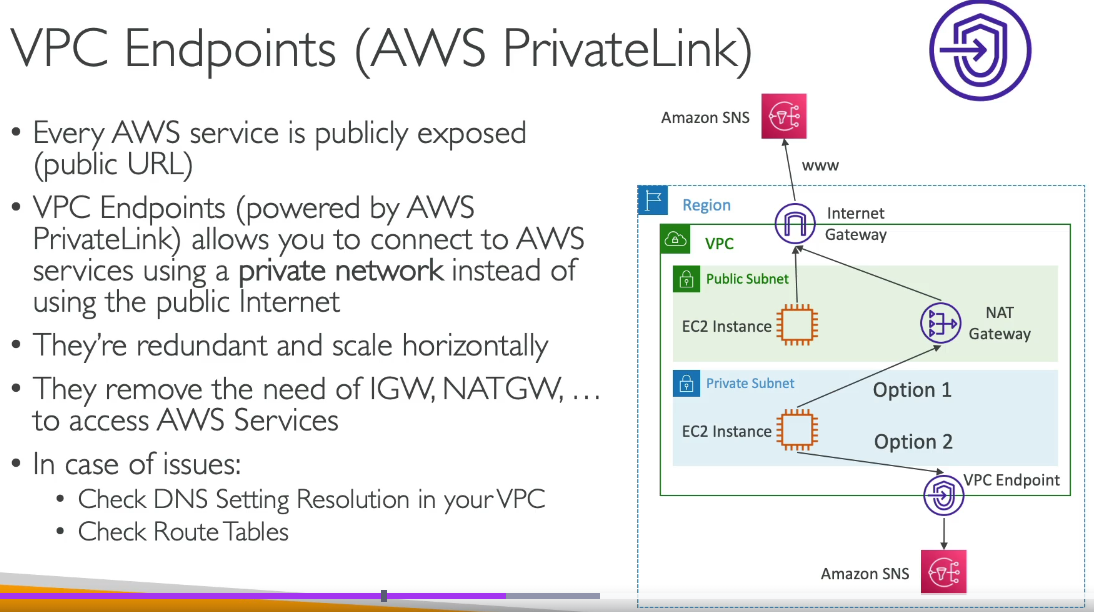
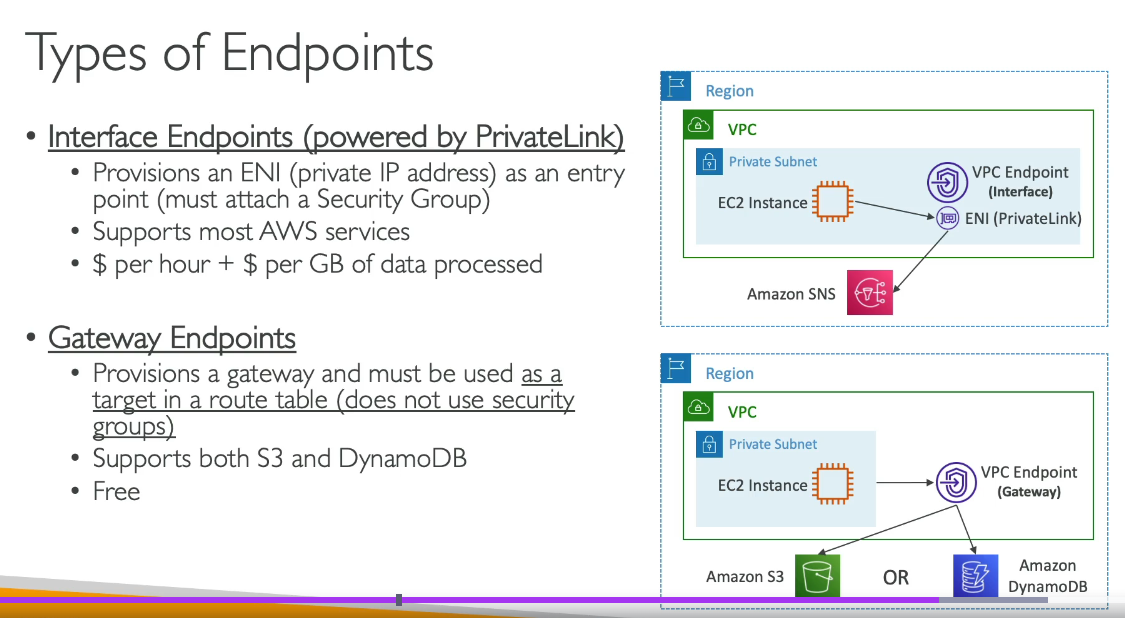
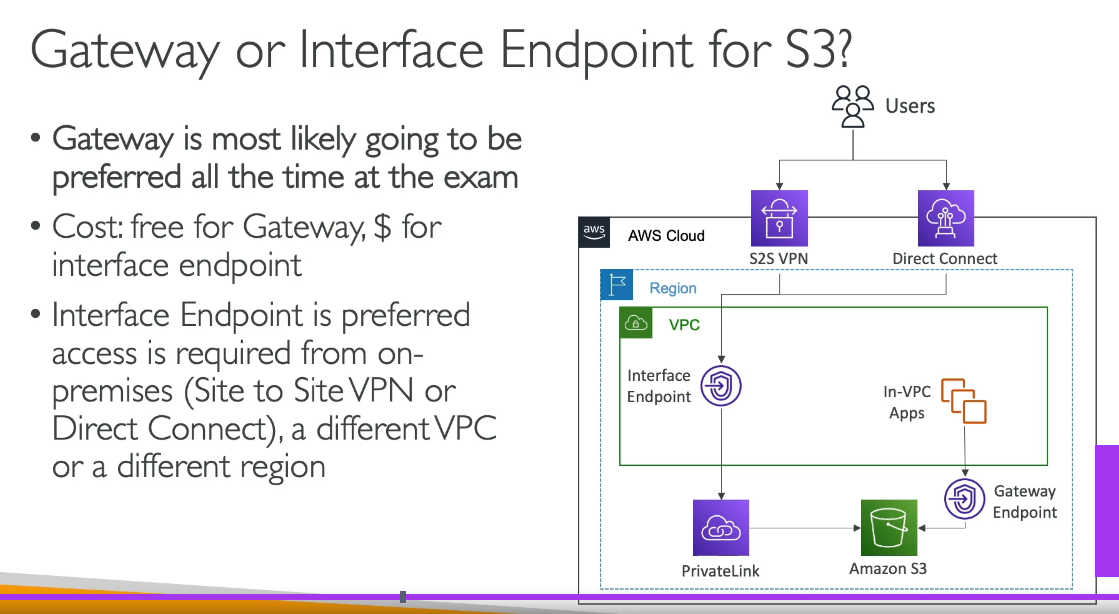
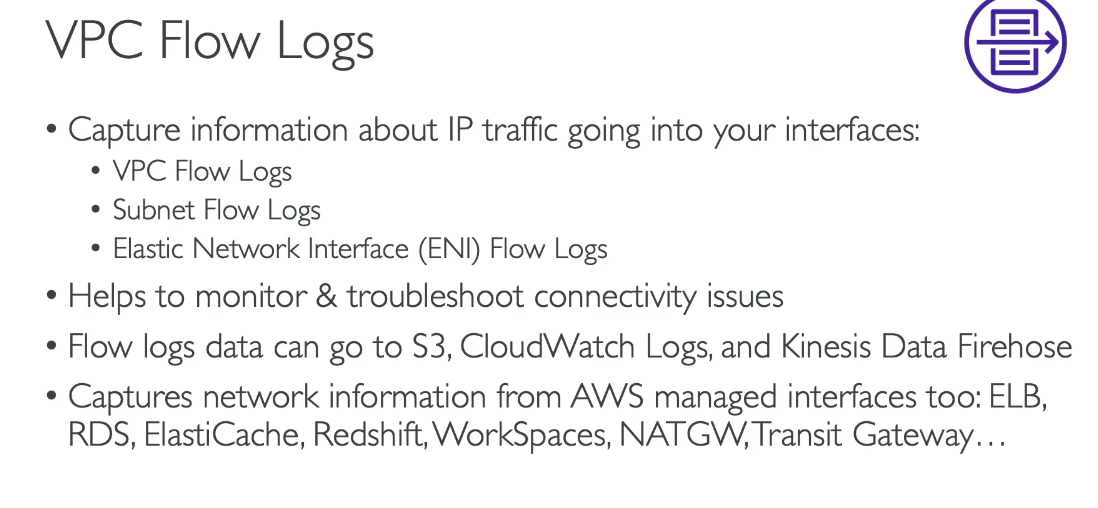
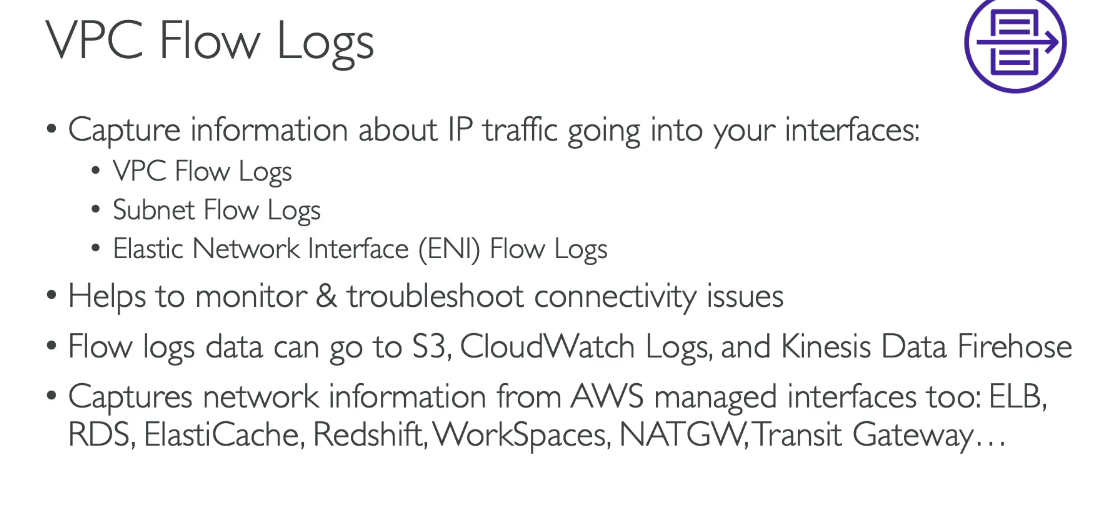

Virtual Private Gateway (VGW) in AWS cannot connect multiple VPCs directly. It is designed to connect a single VPC to an on-premises network over a VPN connection or Direct Connect link.
However, there are several ways to achieve connectivity between multiple VPCs, including using a Virtual Private Gateway as part of a larger solution. Here are the most common methods:
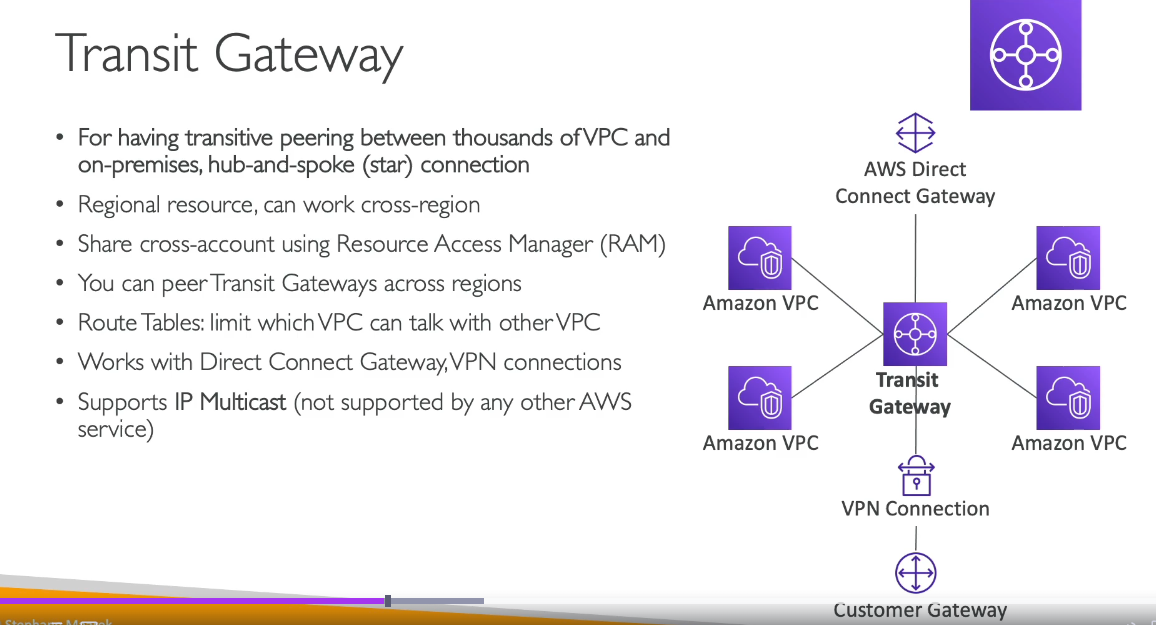
1. Transit Gateway
- The AWS Transit Gateway allows you to connect multiple VPCs to a central gateway. It acts as a hub for inter-VPC communication and can connect VPCs across different regions, along with on-premises networks via Direct Connect or VPN.
- A Transit Gateway can replace multiple peering connections and simplify network management.
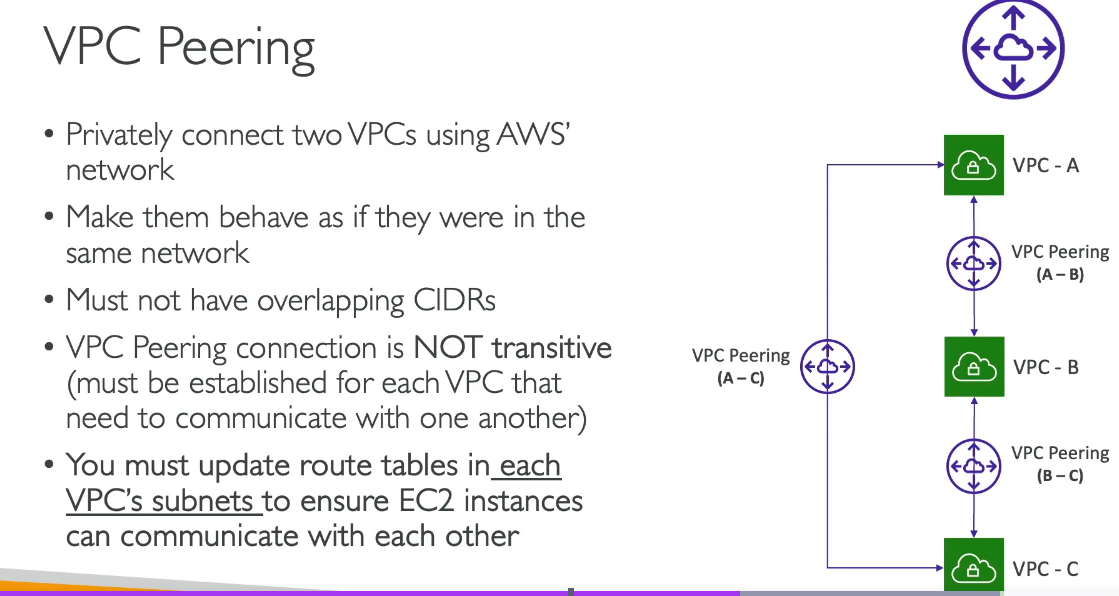
2. VPC Peering
- You can peer VPCs with each other. VPC Peering connects two VPCs, allowing them to route traffic between each other. This can be used for VPC-to-VPC communication, but it’s one-to-one (i.e., one peering connection per VPC pair).
- If you need to connect more than two VPCs, you’d need to create additional peering connections between the VPCs.
3. VPN with Multiple VPCs
- Although the Virtual Private Gateway connects only one VPC to a VPN or Direct Connect, you can set up a VPN connection between each VPC and the on-premises network, or connect multiple VPCs to a central hub VPC using VPC Peering or Transit Gateway.
4. Shared Services VPC
- Another architecture approach is to have a Shared Services VPC. This VPC connects to other VPCs (via VPC Peering or Transit Gateway) and serves as a central location for resources like a shared database, DNS, or other services.
Key Takeaways:
- Virtual Private Gateway (VGW) is meant for a single VPC to an on-premises connection, not multiple VPCs.
- For multiple VPCs, consider using Transit Gateway, VPC Peering, or other solutions like Shared Services VPC.
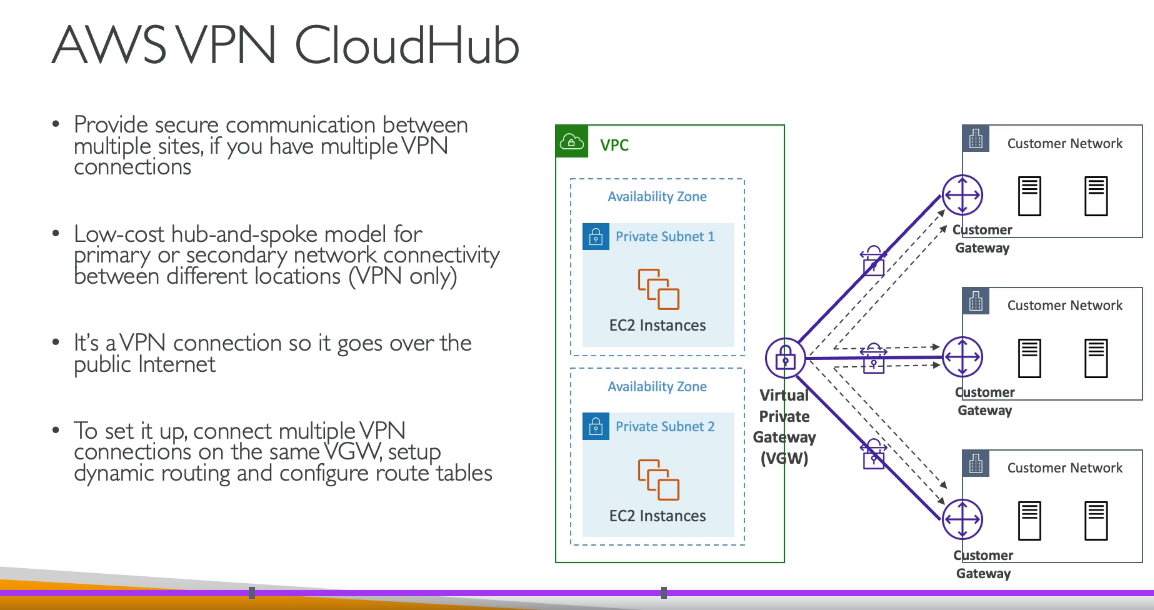
AWS VPN CloudHub
AWS VPN CloudHub is a feature of AWS Site-to-Site VPN that allows you to connect multiple remote networks (e.g., on-premises networks, branch offices) securely over the AWS global network. It uses AWS Virtual Private Gateways (VGW) to establish VPN connections between multiple remote sites and AWS, enabling communication between those sites via AWS.
CloudHub is ideal for scenarios where you need to securely connect multiple on-premises networks or branch offices to each other through AWS.
How AWS VPN CloudHub Works
AWS VPN CloudHub works by creating Site-to-Site VPN connections between your on-premises VPN devices and an AWS Virtual Private Gateway (VGW). It leverages AWS’s global network to route traffic between different VPN connections.
- VPN Connections: You set up Site-to-Site VPN connections from each on-premises network or branch office to an AWS Virtual Private Gateway.
- VPN Tunnels: Each Site-to-Site VPN connection has two VPN tunnels for redundancy and failover.
- VPN CloudHub: Traffic between remote sites flows securely through AWS, routing the traffic via the AWS VPN CloudHub (AWS VGW) to the other connected VPNs. This is done over the AWS global network.
You can use VPN CloudHub to connect up to 50 remote networks (including on-premises networks, branch offices, etc.), all connected to the same AWS Virtual Private Gateway.
Key Benefits of AWS VPN CloudHub
- Secure Communication Between Remote Sites:
- CloudHub allows remote sites (on-premises networks or branch offices) to communicate securely with each other over AWS’s global infrastructure.
- Cost-Effective:
- Rather than deploying direct point-to-point connections or complex MPLS (Multiprotocol Label Switching) networks, AWS VPN CloudHub offers a simpler, more affordable option using existing Site-to-Site VPN connections.
- High Availability:
- VPN CloudHub leverages redundant VPN tunnels for each VPN connection. In case one tunnel fails, traffic is routed over the other tunnel, ensuring high availability and fault tolerance.
- Simple Setup:
- You only need to configure VPN connections from each remote site to AWS, and AWS handles the routing and networking between sites.
- Scalability:
- CloudHub can scale to connect multiple remote sites, making it ideal for enterprises with distributed branch offices or global operations.
Typical Use Cases for AWS VPN CloudHub
- Connecting Multiple Branch Offices to AWS:
- If you have multiple branch offices in different regions and need them to communicate with each other securely, you can use VPN CloudHub to route traffic through AWS.
- Securely Connecting On-Premises Data Centers:
- AWS VPN CloudHub can be used to securely link multiple on-premises data centers over AWS, without needing complex networking infrastructure.
- Global Connectivity:
- CloudHub is useful for businesses that have offices or networks in various geographic regions. AWS’s global infrastructure allows traffic between remote sites to travel securely without the need for expensive and complicated private networking.
Setting Up AWS VPN CloudHub
- Create a Virtual Private Gateway (VGW):
- Create a VGW in the AWS region where your primary VPC is located.
- The VGW serves as the central hub for VPN connections to on-premises networks.
- Establish Site-to-Site VPN Connections:
- Set up Site-to-Site VPN connections from each of your remote networks (on-premises or branch offices) to the VGW in AWS.
- Each VPN connection requires two VPN tunnels for redundancy.
- Configure Routing:
- Configure route tables in each connected network (both on-premises and in AWS) to ensure that traffic between remote sites is routed via the AWS VPN CloudHub.
- AWS automatically handles the routing between VPN connections once they are established.
- Verify Connectivity:
- Test the connectivity between remote networks by ensuring that traffic can flow between them through AWS.
Limitations of AWS VPN CloudHub
- Requires Site-to-Site VPN Connections:
- CloudHub works only with Site-to-Site VPN connections. You cannot use Direct Connect or other types of VPN for CloudHub.
- No Transit Between VPCs:
- AWS VPN CloudHub allows you to connect on-premises or branch office networks to each other, but it doesn’t allow direct communication between VPCs. For VPC-to-VPC connectivity, you would need to use VPC Peering or Transit Gateway.
- Maximum Number of Connections:
- CloudHub supports up to 50 VPN connections to a single Virtual Private Gateway.
Best Practices for AWS VPN CloudHub
- Redundancy:
- Always configure dual VPN tunnels for each connection to ensure high availability. AWS automatically routes traffic to the available tunnel if one goes down.
- Monitor VPN Health:
- Use Amazon CloudWatch to monitor the health and status of your VPN connections to ensure they’re working properly.
- Routing and Security:
- Ensure that proper routing tables are set up in both AWS and on-premises environments to allow the traffic to flow correctly.
- Use security policies (e.g., encryption, authentication) for your VPN connections to ensure data is protected.
- Scalable Connections:
- While AWS VPN CloudHub allows you to connect multiple sites, consider AWS Transit Gateway for more complex scenarios with large-scale, dynamic VPC-to-VPC connections.
Summary
AWS VPN CloudHub is a powerful and cost-effective way to connect multiple remote networks (e.g., branch offices, on-premises data centers) to each other securely through AWS. By using Site-to-Site VPN connections and a Virtual Private Gateway, you can create a secure communication hub for all your remote sites, leveraging AWS’s global infrastructure.
If you’re connecting multiple branch offices or need a simple, scalable way to allow secure communication between remote networks, AWS VPN CloudHub is a great solution. However, for more complex networking needs, like connecting VPCs, you might want to explore alternatives like AWS Transit Gateway.
Let me know if you need more details on setup or other AWS networking solutions!