AWS WAF is a managed web application firewall service that helps protect your web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. It allows you to create custom security rules to block or allow traffic based on specific conditions, such as IP addresses, HTTP headers, request body, URI strings, and more.
AWS WAF is integrated with other AWS services such as Amazon CloudFront, Application Load Balancer (ALB), API Gateway, and AWS App Runner, providing a comprehensive security solution for web applications hosted on AWS.
Key Features of AWS WAF:
Customizable Rules:
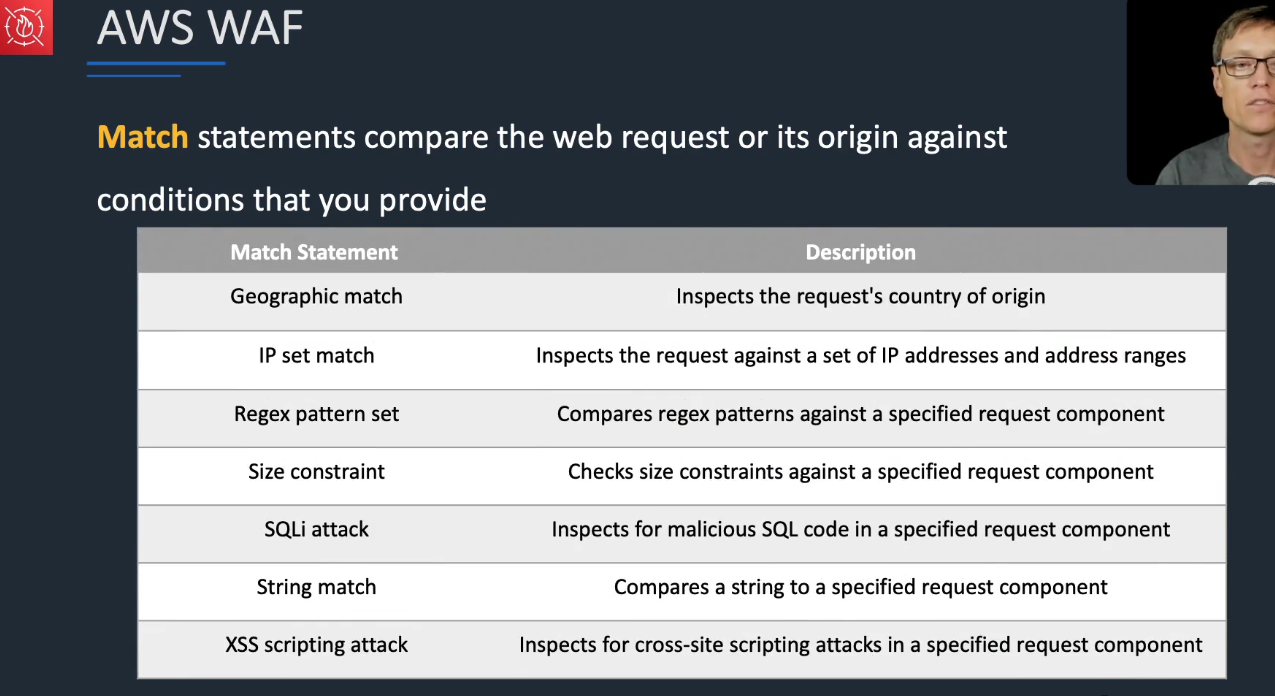
You can create custom rules to allow or block web traffic based on various criteria such as:
- IP addresses
- Geographical location
- Request headers
- Request body
- URI paths
- Query strings
Predefined Managed Rule Groups:
AWS provides predefined managed rule groups that offer protection against common threats, including:
- SQL injection attacks
- Cross-site scripting (XSS)
- Web application attacks like OWASP top 10 risks
These rules are continuously updated by AWS security experts, allowing you to easily protect your application without manual intervention.
Rate Limiting (Rate-based Rules):
AWS WAF supports rate-based rules that allow you to set thresholds for the number of requests coming from a specific IP address. If a threshold is exceeded, the requests from that IP address can be blocked temporarily. This feature is useful to prevent DDoS attacks or brute force attempts.
Integration with Amazon CloudFront:
AWS WAF can be integrated with Amazon CloudFront, the global content delivery network (CDN) service, to provide a distributed firewall that protects your application at the edge.
CloudFront integrates with AWS WAF to allow or block traffic before it reaches your application servers.
Real-time Visibility and Monitoring:
AWS WAF offers real-time visibility into web traffic and security events. You can monitor and log all requests that are inspected by WAF, which helps to detect malicious traffic and analyze attack patterns.
It integrates with Amazon CloudWatch for logging and metrics, enabling alerting and detailed traffic analysis.
Web ACLs (Access Control Lists):
AWS WAF uses Web ACLs to define sets of rules that specify which requests to allow, block, or count. You can attach a Web ACL to CloudFront, ALB, or API Gateway to filter the traffic before reaching your web application.
Each Web ACL can have multiple rules (both allow and block), and they can be evaluated in the order you specify.
Bot Control:
AWS WAF provides bot control features to detect and mitigate bot traffic, such as scrapers, brute force attacks, and credential stuffing.
Bot control mechanisms can be based on reputation lists, machine learning, and other techniques to identify bad bots.
Protection Against DDoS:
AWS WAF helps mitigate large-scale Distributed Denial of Service (DDoS) attacks, especially when combined with AWS Shield, which provides additional layers of protection.
You can configure rate-based rules and monitor for unusual spikes in web traffic to reduce the risk of DDoS attacks impacting your web applications.
Flexible and Scalable:
AWS WAF is fully managed, scalable, and flexible, meaning you don’t need to manage any infrastructure or worry about scaling your firewall as your traffic grows.
How AWS WAF Works:
Web ACL Creation:
You start by creating a Web ACL in AWS WAF. A Web ACL is a collection of rules that define what traffic is allowed, blocked, or counted.
Rule Configuration:
You define rules in the Web ACL. These rules specify conditions to inspect incoming HTTP requests. The conditions could be based on:
- IP addresses
- Request headers
- URI strings
- Request body content
- Query strings
- Geolocation
- Rate limits
Web Traffic Inspection:
Once the Web ACL is configured, you associate it with AWS resources such as Amazon CloudFront or an Application Load Balancer (ALB).
AWS WAF inspects each incoming request to your web application, checking it against the rules defined in the Web ACL.
Action on Requests:
Based on the evaluation of each request, AWS WAF takes action according to the rule configuration:
- Allow: The request is allowed to proceed to your application.
- Block: The request is blocked, and the client receives an HTTP 403 response.
- Count: The request is allowed, but the request is logged for monitoring and analysis without blocking.
Logging and Metrics:
All the requests and actions are logged to Amazon CloudWatch or Amazon Kinesis Data Firehose, providing you with detailed insights into traffic patterns and security threats.
Protection Against Attacks:
With AWS WAF in place, malicious traffic (e.g., SQL injection, XSS) can be blocked, and harmful bots or DDoS attacks can be mitigated before they reach your web application.