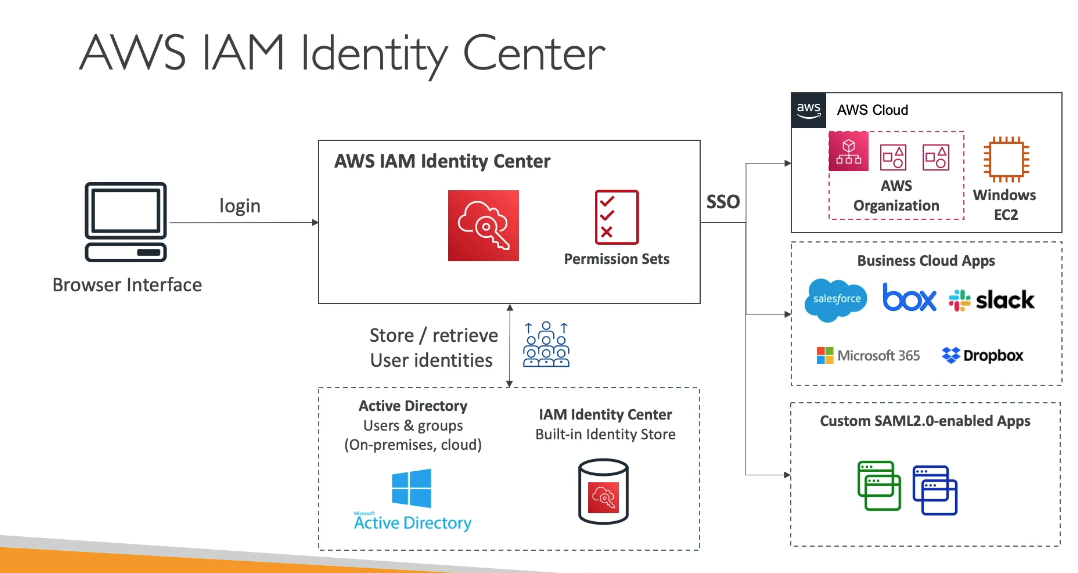
AWS Identity Center (formerly AWS Single Sign-On) is a service that enables centralized identity and access management across multiple AWS accounts and cloud applications. It provides a way to manage user authentication, authorization, and access control efficiently.
Key Features of AWS Identity Center:
- Centralized User Management – Manage user access to AWS accounts and applications from a single location.
- Integration with Identity Providers – Supports Microsoft Entra ID (formerly Azure AD), Okta, Google Workspace, and other SAML 2.0 providers.
- Multi-Account Access – Assign and manage permissions across AWS Organizations.
- User Authentication – Supports built-in user directory or external identity providers.
- Fine-Grained Access Control – Uses AWS IAM Identity Center Permission Sets to define access levels.
- Single Sign-On (SSO) – Provides a single access point for multiple AWS accounts and applications.
- Multi-Factor Authentication (MFA) – Enhances security with additional authentication methods.
Common Use Cases:
- Providing employees access to multiple AWS accounts securely.
- Enforcing least privilege access with IAM permission sets.
- Integrating with existing corporate identity systems (e.g., Microsoft Entra ID, Okta).
- Enabling seamless single sign-on (SSO) for cloud applications.
AWS Identity Center consists of several key components that work together to manage identities and access across AWS accounts and applications.
Main Components of AWS Identity Center:
1. Users and Groups
- You can create and manage users and groups within AWS Identity Center.
- Users can be sourced from:
- The built-in AWS Identity Center directory.
- An external identity provider (IdP) like Microsoft Entra ID, Okta, or Google Workspace via SAML 2.0.
2. Identity Providers (IdP)
- Supports integration with third-party IdPs for authentication.
- Can connect via Security Assertion Markup Language (SAML) 2.0 or System for Cross-domain Identity Management (SCIM) for automatic user provisioning.
3. Permission Sets
- Predefined sets of IAM permissions that control user access to AWS accounts and services.
- Examples: AdministratorAccess, ReadOnlyAccess, or custom policies.
4. Account Assignments
- Users and groups are assigned permission sets to specific AWS accounts.
- Allows fine-grained access control across multiple accounts in an AWS Organization.
5. Application Access
- Enables users to sign in to third-party cloud applications (e.g., Salesforce, Office 365) via SSO.
- Configured using SAML 2.0 authentication.
6. AWS Access Portal
- A web-based interface where users log in to access AWS accounts and applications.
- Provides a centralized dashboard for managing access.
7. Multi-Factor Authentication (MFA)
- Supports MFA for enhanced security.
- Can enforce MFA policies for users accessing AWS resources.
Relationship Between AWS Identity Center and Identity Federation
AWS Identity Center plays a crucial role in identity federation, allowing organizations to manage authentication and authorization for AWS resources using external identity providers (IdPs).
How Identity Federation Works with AWS Identity Center
Identity federation enables users to log in to AWS services using their existing credentials from an external identity provider (e.g., Microsoft Entra ID, Okta, Google Workspace). This eliminates the need to create separate AWS IAM users.
- User Authentication
- Users authenticate with their organization’s identity provider (IdP).
- AWS Identity Center supports SAML 2.0 and SCIM for federated authentication and user provisioning.
- Identity Center as the Broker
- AWS Identity Center acts as the central broker between AWS and the external IdP.
- After authentication, Identity Center assigns permission sets to users, defining their access levels within AWS accounts.
- Authorization via Permission Sets
- Once authenticated, users receive temporary credentials to access AWS services.
- Identity Center assigns permission sets based on group memberships or roles from the IdP.
- Single Sign-On (SSO) Access
- Users access AWS accounts and third-party applications through the AWS Access Portal.
- This simplifies access management across multiple AWS accounts.
Benefits of Identity Federation with AWS Identity Center
✅ Centralized User Management – Use existing identities from your corporate IdP.
✅ Enhanced Security – Enforce MFA and conditional access policies.
✅ No IAM User Overhead – Eliminates the need to manually create and manage IAM users.
✅ Seamless Access – Users sign in once and get access to AWS resources and third-party applications.