Feature of S3, simplify data access for any AWS service or customer application that stores data in S3. With S3 Access Points, customers can create unique access control policies for each access point to easily control access to shared datasets.
You can access data in shared buckets through an access point in one of two ways. For S3 object operations, you can use the access point ARN in place of a bucket name. For requests requiring a bucket name in the standard S3 bucket name format, you can use an access point alias instead. Aliases for S3 Access Points are automatically generated and are interchangeable with S3 bucket names anywhere you use a bucket name for data access.
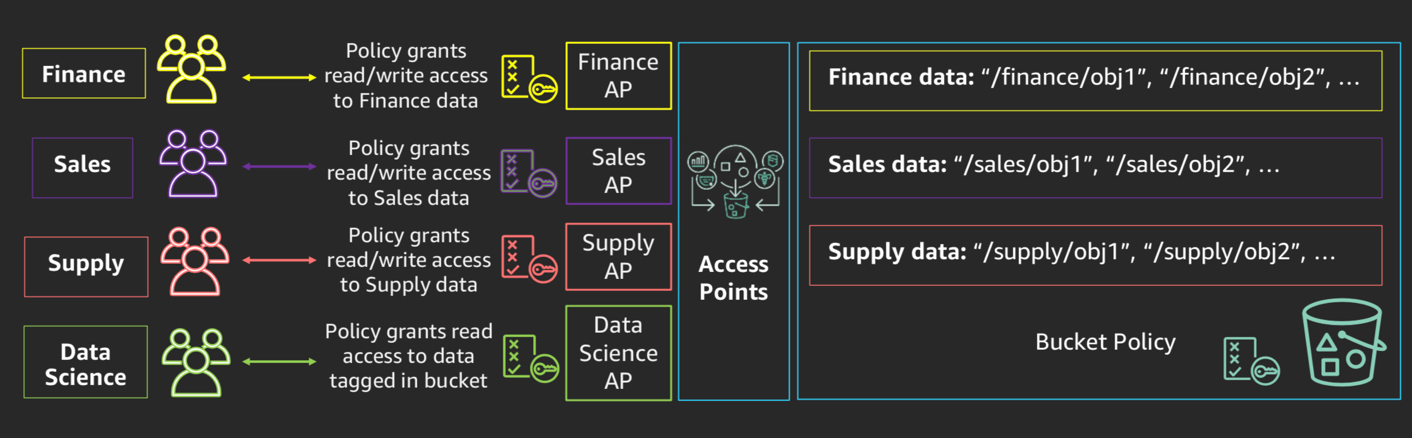
Customizable Access Control: Each access point has its own access policy, which can define who can access the data and under what conditions. This is particularly useful for fine-grained access management.
Unique DNS Name: Each access point is assigned a unique DNS name. You can use this DNS name to access the data in the associated S3 bucket. The format of the access point’s DNS name is:
phpCopy<access-point-name>-<account-id>.s3-accesspoint.amazonaws.com
Simplified Permissions: Access Points allow for simplified management of permissions for specific applications, removing the need to manually configure IAM policies for each user or application. Access Points use IAM policies and bucket policies to manage access but also provide an additional layer of abstraction.
Data Access Control by Use Case: Access Points can be created with specific use cases in mind. For example, you can create one for:
- An application running on EC2.
- A group of users accessing data in S3 through a specific access point.
- Services like Amazon EMR, Amazon SageMaker, or Amazon Redshift that need specialized access.
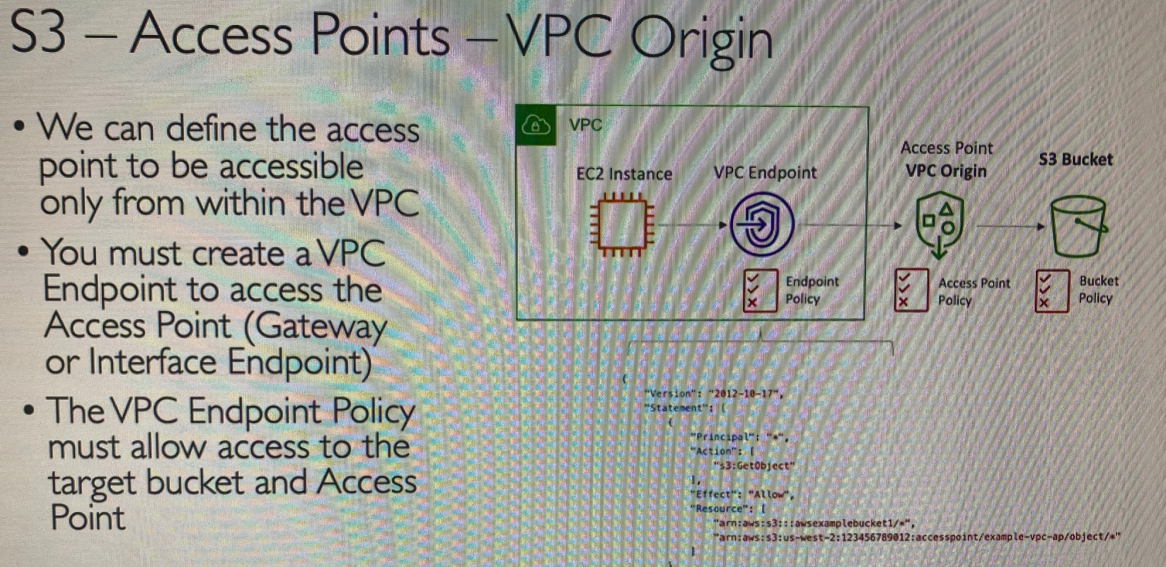
VPC-Enabled Access Points: You can configure access points to be used from within a Virtual Private Cloud (VPC). This allows you to restrict access to data only to resources that are within the same VPC, adding an extra layer of security by ensuring that no traffic from outside the VPC can access the data.
Access Point Policies: These policies can control what users can do with objects in a specific access point, such as read or write operations. You can set these policies for specific actions or restrict access to certain prefixes (paths) within a bucket.