Point of Presence vs Edge Location
Point of Presence (PoP) and an Edge Location are not the same, although they are related concepts in network architecture.
- Point of Presence (PoP): A PoP typically refers to a physical location, facility, or data center where two or more networks or communication devices share a connection.
- Edge Location: Edge locations are specific sites or data centers designed to deliver web content and services closer to users to reduce latency. These locations are usually part of a larger CDN distribution and are optimized for caching and delivering content to end-users efficiently.
https://www.ioriver.io/questions/is-point-of-presence-same-as-edge-location
Cloudfront
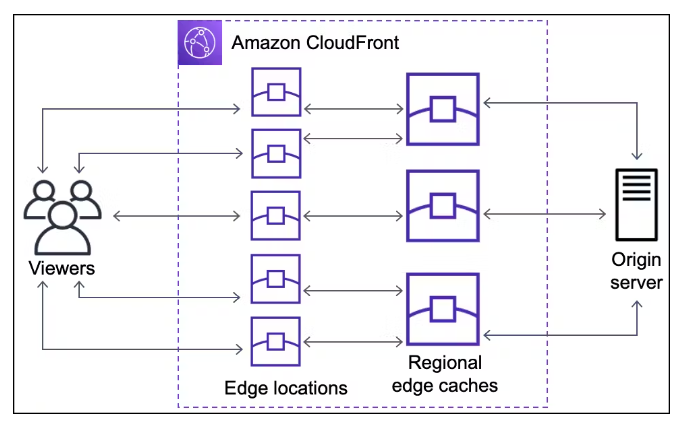
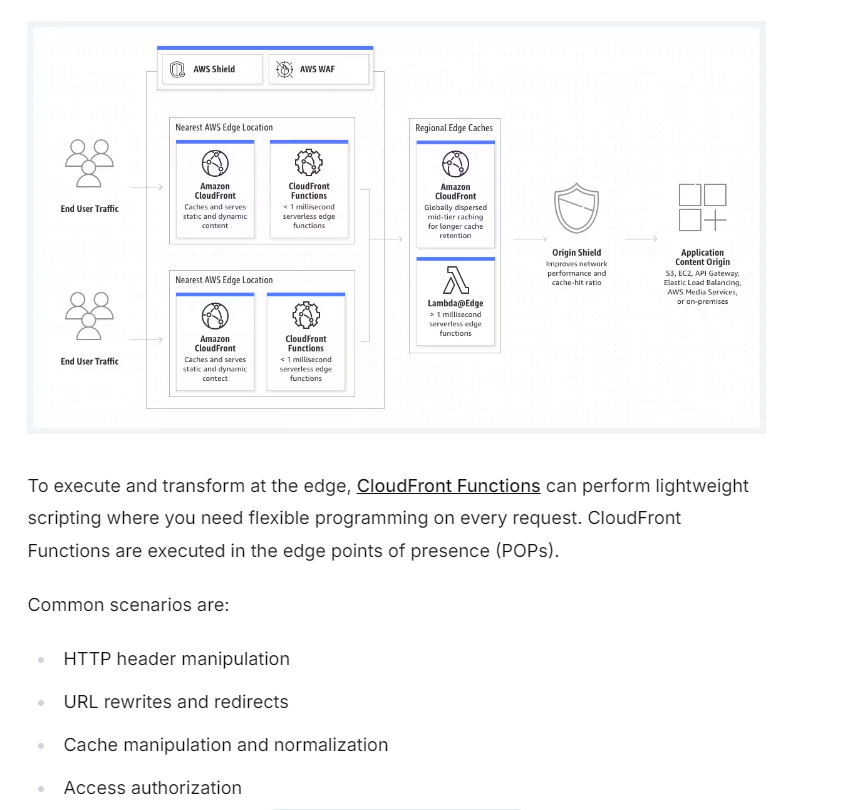
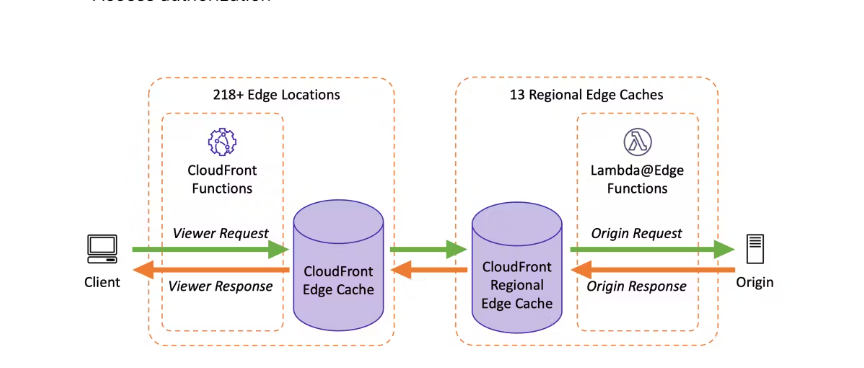
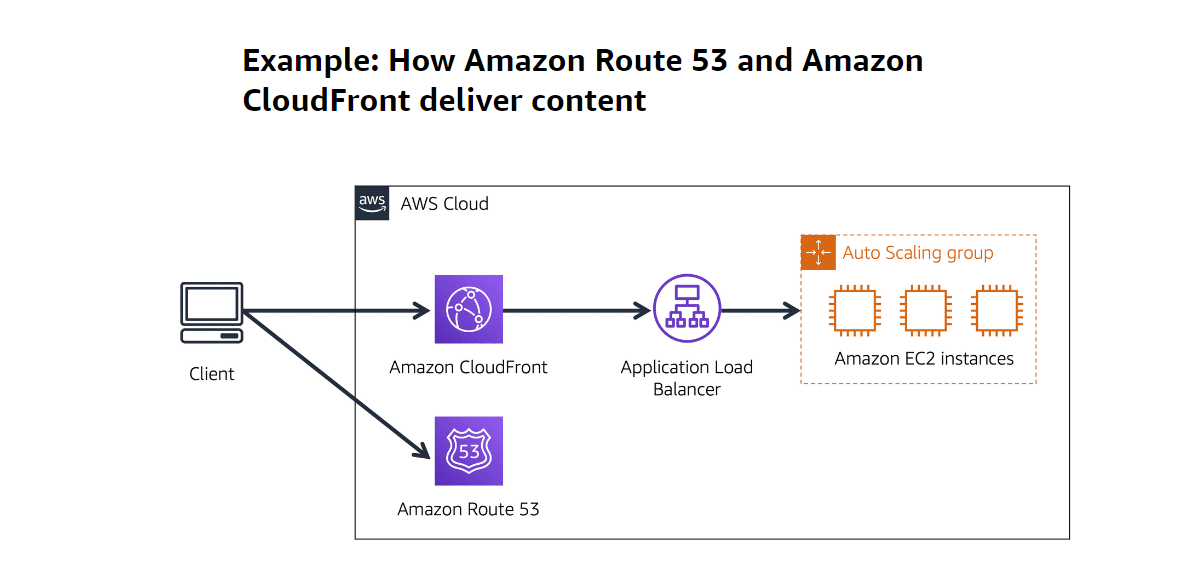
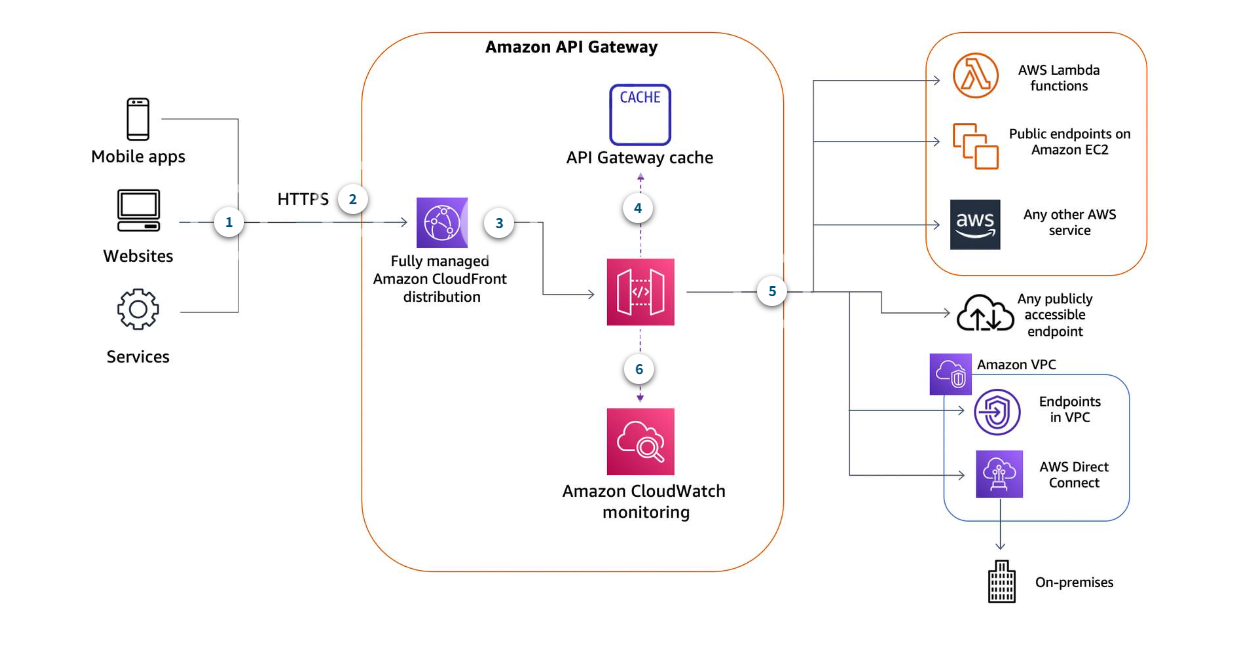
Lambda@Edge
is an extension of AWS Lambda that allows you to run functions in response to CloudFront events. It enables you to execute custom logic closer to your end users, at CloudFront edge locations worldwide, thereby reducing latency and improving the performance of your applications.
Overview of Lambda@Edge:
Lambda@Edge allows you to run Lambda functions that can modify requests and responses as they pass through CloudFront edge locations. It is ideal for scenarios where you want to customize how CloudFront serves content or handle specific logic at the edge, such as dynamic content generation, authentication, or A/B testing.
Key Features:
- Runs at Edge Locations:
- Lambda functions are executed at CloudFront’s globally distributed edge locations, meaning that your functions are closer to the end users, which results in lower latency and faster performance.
- Custom Request/Response Handling:
- You can modify incoming HTTP requests before they reach your origin, or modify responses from the origin before they are returned to the client.
- This allows you to perform tasks like URL rewrites, header manipulation, or dynamic content generation.
- Event-driven Execution:
- Lambda@Edge functions are triggered by CloudFront events such as:
- Viewer Request: When a request is made by the viewer (end user) to CloudFront.
- Origin Request: When a request is forwarded to the origin (your server, S3, or other backend).
- Origin Response: When the response is returned from the origin.
- Viewer Response: Before the response is sent to the viewer.
- Lambda@Edge functions are triggered by CloudFront events such as:
- Global Scalability:
- Lambda@Edge functions are automatically replicated across CloudFront’s global edge network. You don’t need to manage any infrastructure; AWS handles the scaling and distribution.
- Security:
- You can use Lambda@Edge for security purposes such as performing user authentication and authorization, validating headers or cookies, and protecting against certain attack vectors.
- Lambda@Edge also integrates with AWS WAF (Web Application Firewall) to provide additional security and filtering at the edge.
- Custom Headers and Redirects:
- You can add, modify, or remove HTTP headers before requests are sent to the origin or before responses are sent to users.
- Redirects and rewrites can be performed on requests and responses (e.g., HTTP to HTTPS, or redirecting based on geographic location).
- Cost-Effective:
- You only pay for the compute time consumed by your Lambda function and the number of executions. There are no charges for idle time or infrastructure maintenance, making it a cost-effective solution for many use cases.
Lambda@Edge Use Cases:
- Content Personalization:
- Customize the content that is served to users based on specific request parameters (such as headers, cookies, or geographical location).
- Example: Modify content dynamically based on user preferences or device type.
- A/B Testing:
- You can implement A/B testing at the edge by routing different traffic to different versions of your content or application.
- Example: Dynamically modify the response to serve different versions of a page depending on the visitor’s session or other criteria.
- SEO (Search Engine Optimization):
- Lambda@Edge can rewrite URLs or add custom headers to help improve SEO for dynamic websites.
- Example: Automatically rewrite URLs for cleaner, search-friendly paths.
- Custom Authentication:
- Perform custom authentication and authorization checks at the edge before users can access certain content.
- Example: Check for a JWT (JSON Web Token) or custom headers in the request to validate user access.
- Content Routing:
- Route requests to different origins or cache behaviors based on specific conditions.
- Example: Route requests for a specific subdomain to a particular server or backend service.
- Security:
- Implement security measures such as preventing DDoS attacks, filtering malicious requests, or masking certain sensitive data in headers or responses.
- Example: Validate tokens, add anti-CSRF tokens, or check for IP blacklisting at the edge.
- Image Optimization:
- Automatically modify image requests to resize, crop, or optimize images before returning them to the user.
- Example: Resize images dynamically based on device type (mobile vs. desktop).