Options
| Option | Use Case | Advantages | Limitations |
|---|---|---|---|
| VPC peering | AWS-provided network connectivity between two VPCs. | Leverages AWS managed scalable networking infrastructure | VPC peering does not support transitive peering relationshipsDifficult to manage at scale |
| AWS Transit Gateway | AWS-provided regional router connectivity for VPCs | AWS managed high availability and scalability serviceRegional network hub for up to 5,000 attachments | Transit Gateway peering only supports static routes |
| AWS PrivateLink | AWS-provided network connectivity between two VPCs using interface endpoints | Leverages AWS managed scalable networking infrastructure | VPC Endpoint services only available in the AWS region in which they are created |
| Software VPN | Software appliance- based VPN connections between VPCs | Supports a wide array of VPN vendors, products, and protocolsManaged entirely by you | You are responsible for implementing HA solutions for all VPN endpoints (if required)VPN instances could become a network bottleneck |
| Software VPN-to-AWS Site-to-Site VPN | Software appliance to VPN connection between VPCs | AWS managed high availability VPC VPN connectionSupports a wide array of VPN vendors and products managed by youSupports static routes and dynamic BGP peering and routing policies | You are responsible for implementing HA solutions for the software appliance VPN endpoints (if required)VPN instances could become a network bottleneckIPsec VPN protocol only to AWS Managed VPN |
VPC peering
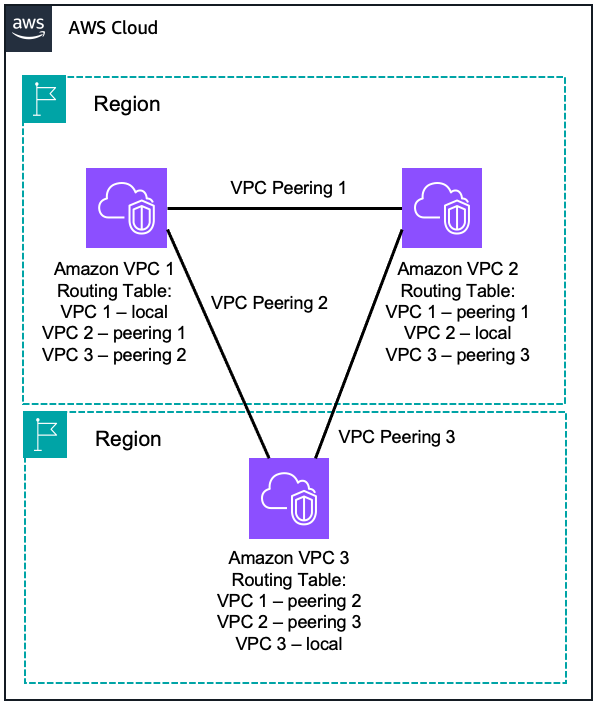
A VPC peering connection is a networking connection between two VPCs that enables routing using each VPC’s private IP addresses as if they were in the same network. VPC peering connections can be created between your own VPCs or with a VPC in another AWS account. VPC peering also supports inter-region peering.
Traffic using inter-region VPC Peering always stays on the global AWS backbone and never traverses the public internet, thereby reducing threat vectors, such as common exploits and DDoS attacks.
AWS uses the existing infrastructure of a VPC to create VPC peering connections and does not rely on a separate piece of physical hardware. Therefore, they do not introduce a potential single point of failure or network bandwidth bottleneck between VPCs. Additionally, VPC routing tables, security groups, and network access control lists can be leveraged to control which subnets or instances are able to utilize the VPC peering connection.
Amazon VPCs do not support transitive peering, meaning that you can’t communicate two VPCs that are not directly peered using a third VPC as transit. If you want all of your VPCs to communicate with each other using VPC peering, you will need to create 1:1 VPC peering connections between each of them. Alternatively, you can use AWS Transit Gateway or AWS Cloud WAN to act as a network transit hub.
Both IPv4 and IPv6 traffic is supported in VPC peering connections. However, two VPCs cannot be peered if their primary IPv4 CIDR block overlaps, regardless of the secondary IPv4 or IPv6 CIDR blocks used. Take this into account when assigning the primary CIDR block to your VPCs if you plan to use VPC peering between them.
AWS Transit Gateway
AWS Transit Gateway is a highly available and scalable service to consolidate the AWS VPC routing configuration for a region with a hub-and-spoke architecture. Each spoke VPC only needs to connect to the Transit Gateway to gain access to other connected VPCs. Both IPv4 and IPv6 traffic is supported in AWS Transit Gateway.
You can take advantage of several Transit Gateway route tables, associations, and propagations to segment your traffic within the same Transit Gateway. You will be able to manage different routing domains (for example, production and non-production traffic) from a single point of management, ensuring that these routing domains won’t be able to communicate between each other.
You can also take advantage of the hub-and-spoke architecture created by Transit Gateway to centralize access to shared services such as traffic inspection, interface VPC endpoint access, or egress traffic through a NAT gateway or NAT instances. This centralization simplifies the complexity of managing these resources in several VPCs, and allow for a better control as you extend your footprint in AWS.
Transit Gateways can be peered with each other within the same AWS Region or between different AWS Regions. AWS Transit Gateway traffic always stays on the global AWS backbone and never traverses the public internet, thereby reducing threat vectors such as common exploits and DDoS attacks.

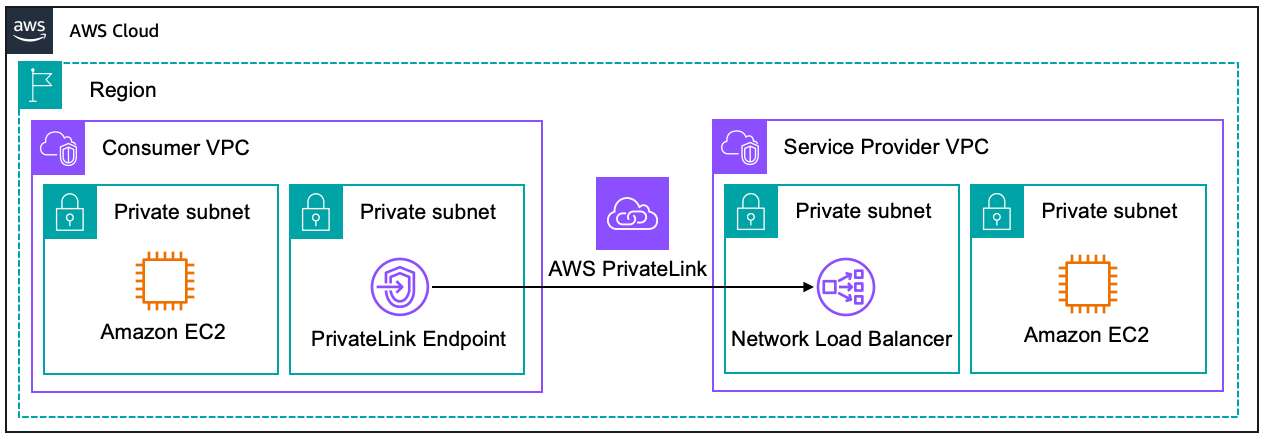
AWS PrivateLink
AWS PrivateLink enables you to connect to some AWS services, services hosted by other AWS accounts (referred to as endpoint services), and supported AWS Marketplace partner services, via private IP addresses in your VPC. The interface endpoints are created directly inside of your VPC, using elastic network interfaces and IP addresses in your VPC’s subnets. That means that VPC Security Groups can be used to manage access to the endpoints.
Software VPN
Amazon VPC provides network routing flexibility. This includes the ability to create secure VPN tunnels between two or more software VPN appliances to connect multiple VPCs into a larger virtual private network so that instances in each VPC can seamlessly connect to each other using private IP addresses. This option is recommended when you want to manage both ends of the VPN connection using your preferred VPN software provider. This option uses an internet gateway attached to each VPC to facilitate communication between the software VPN appliances.
You can choose from an ecosystem of multiple partners and open source communities that have produced software VPN appliances that run on Amazon EC2. Along with this choice comes the responsibility for you to manage the software appliance including configuration, patches, and upgrades.
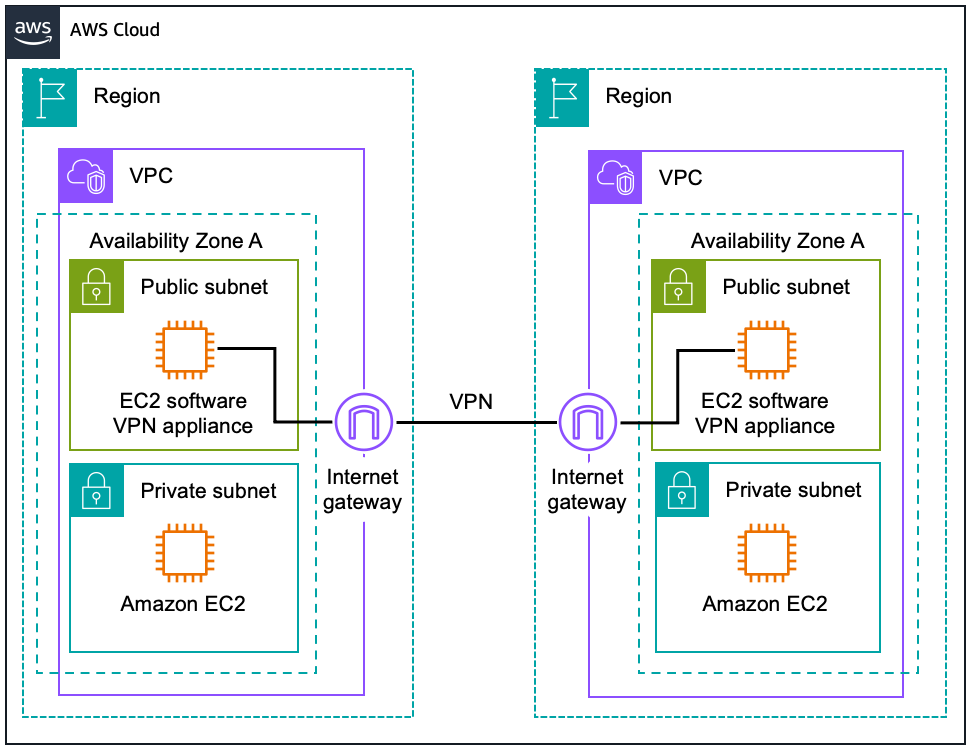
Software VPN-to-AWS Site-to-Site VPN
Amazon VPC provides the flexibility to combine the AWS managed VPN and software VPN options to connect multiple VPCs. With this design, you can create secure VPN tunnels between a software VPN appliance and a virtual private gateway, allowing instances in each VPC to seamlessly connect to each other using private IP addresses.
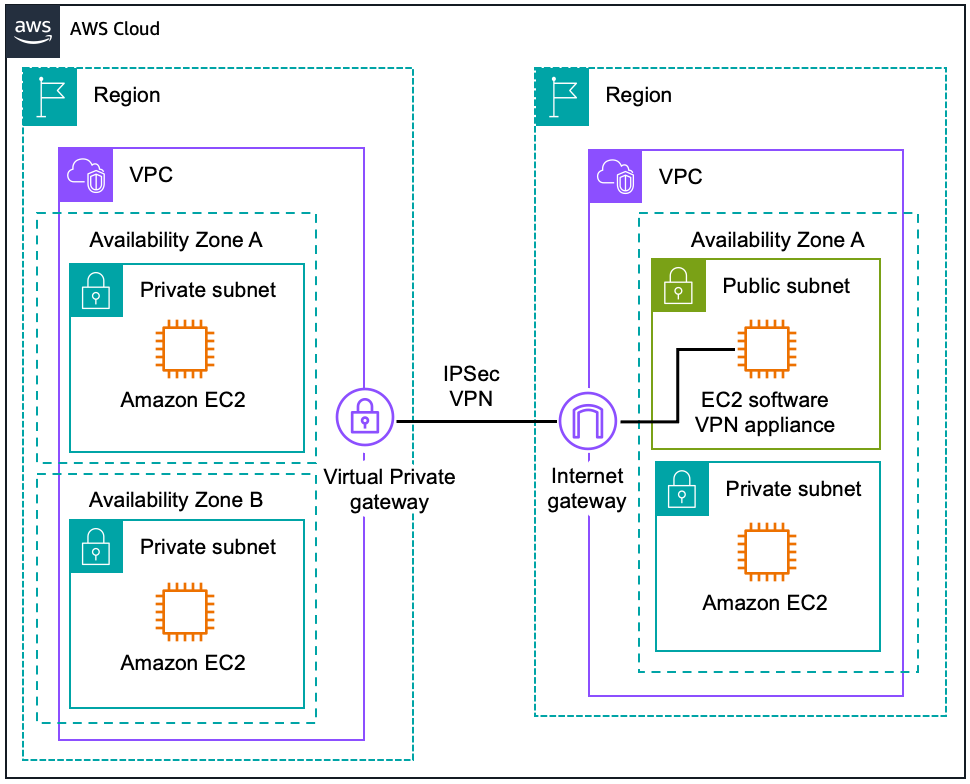
Software remote access-to-Amazon VPC
| Option | Use Case | Advantages | Limitations |
|---|---|---|---|
| AWS Client VPN | AWS managed remote access solution to Amazon VPC and/or internal networks | AWS managed high availability and scalability service | OpenVPN clients only |
| Software client VPN | Software VPN appliance remote access solution to Amazon VPC and/or internal networks | Supports a wider array of VPN vendors, products, and protocolsFully customer-managed solution | You are responsible for implementing HA solutions |
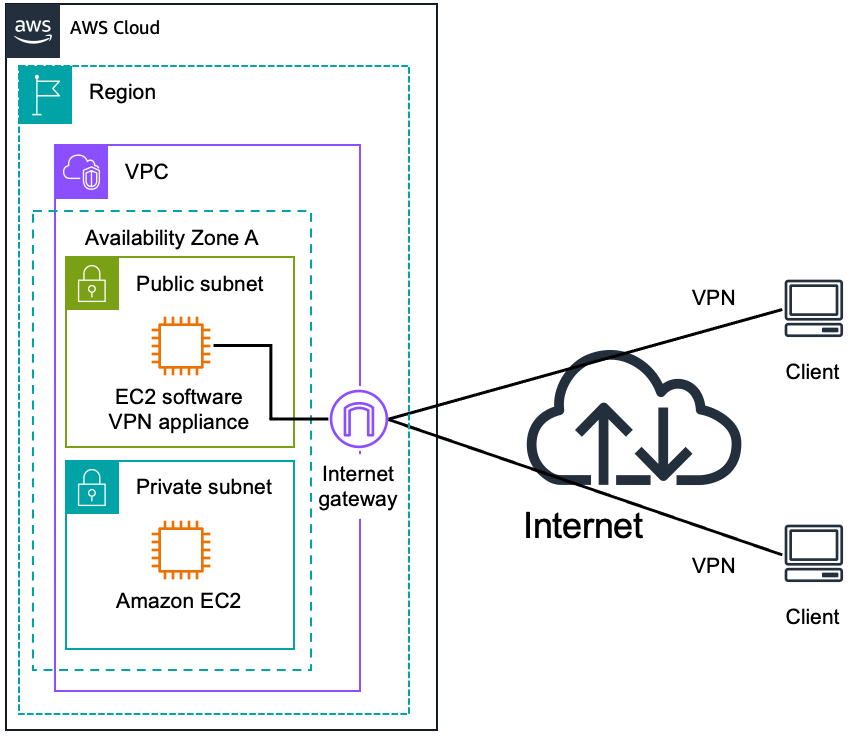
AWS Client VPN
AWS Client VPN is an AWS managed high availability and scalability service enabling secure software remote access. It provides the option of creating a secure TLS connection between remote clients and your Amazon VPCs, to securely access AWS resources and on-premises over the internet
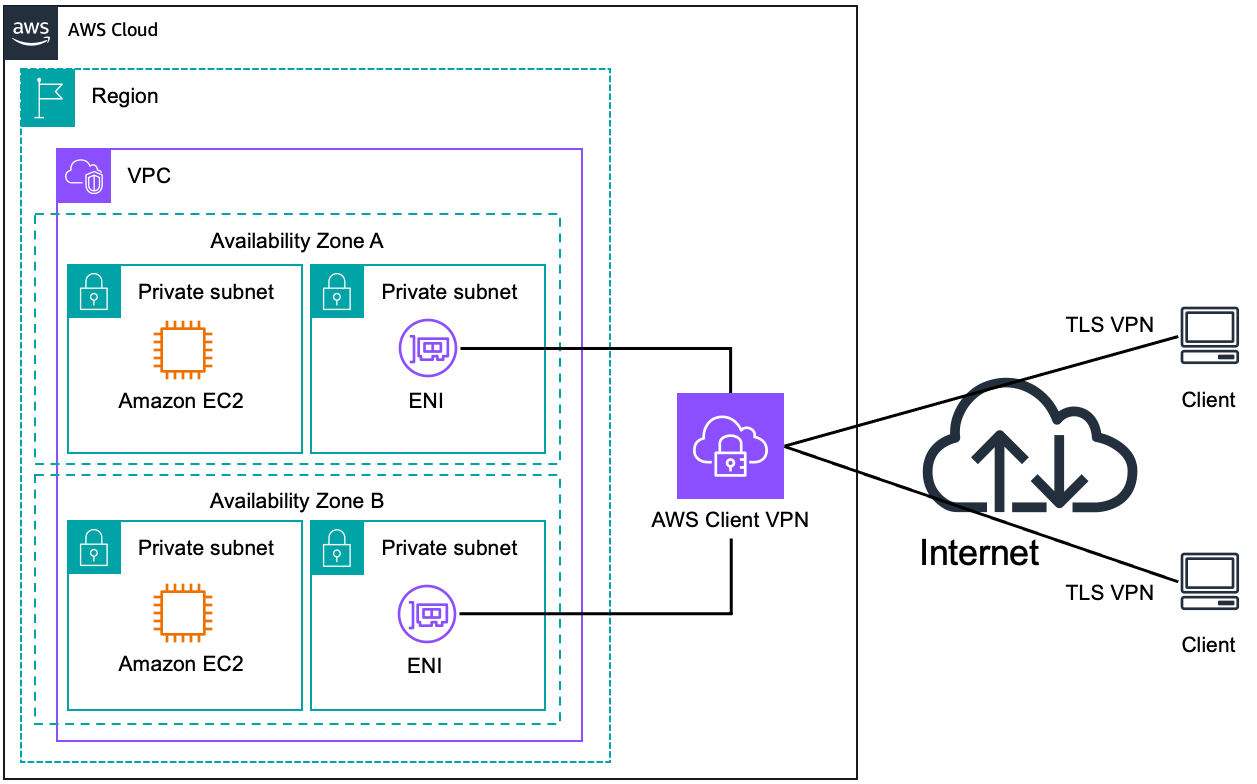
Software client VPN
You can choose from an ecosystem of multiple partners and open source communities that have produced remote-access solutions that run on Amazon EC2. These solutions provide great flexibility on the security protocol use for remote-access into your Amazon VPCs, to securely access AWS resources and on-premises over the internet